Online security has become an essential necessity because of the digital transformation which our world currently experiences. Virtual Private Networks (VPNs) are widely utilized by users to secure their internet connection and keep their information private. The article demonstrates VPN functionality by describing encryption and tunnelling as essential components. This piece examines VPN terminology and its combined importance and operational aspects in establishing secure online conditions.
Table of Contents
What Is a VPN?
The service known as VPN or Virtual Private Network establishes a protected connection between your devices and the internet network. The VPN provider operates servers that connect encrypted online traffic from users through a protected tunnel. The VPN service creates a secure connection that conceals your original IP address and protects the activities you do online from hackers and internet service providers. VPN operates as a confidential network route that protects online users in the unpredictable internet environment.
The Need for VPNs
With growing cyber threats and heightened online privacy concerns, VPNs are now a must for the majority of internet users. Remote workers accessing public Wi-Fi hotspots such as coffee shops and homes are vulnerable to having their information intercepted. Through VPNs, such protection exists for financial data along with personal email correspondence because unauthorized users encounter significant difficulties accessing your information. The ability to browse anonymously through VPNs becomes essential in locations which limit online freedom.
How Does a VPN Work?
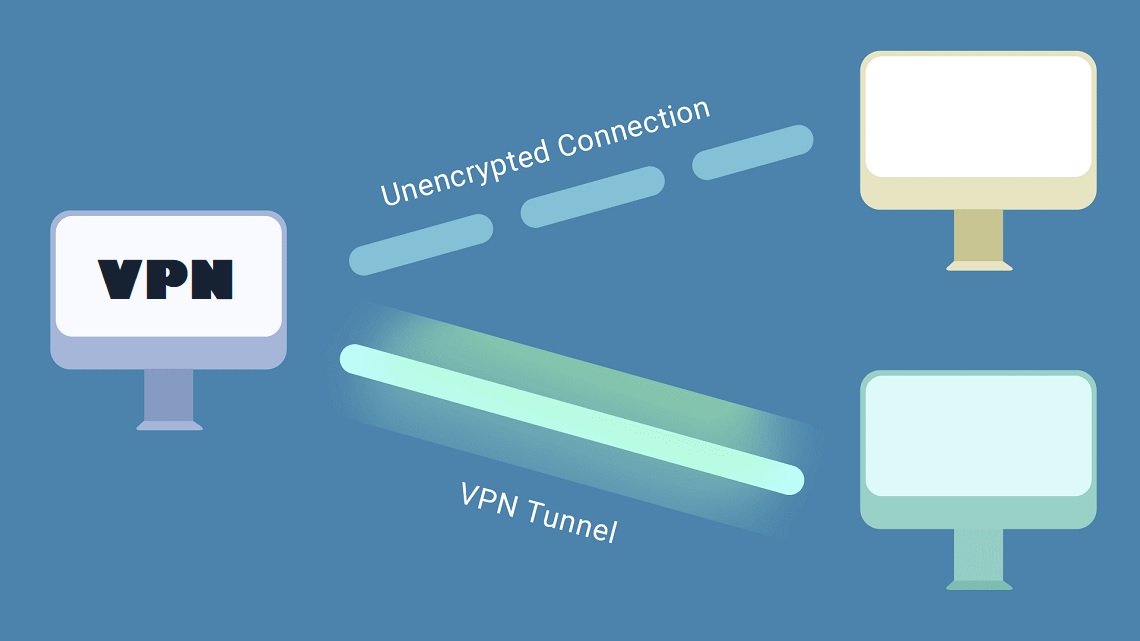
The core functionality of a VPN creates a protected encrypted connection between your device and the VPN server. The secure encrypted link between devices and VPN servers operates under the name of “tunnel.” After establishing the tunnel, every piece of data travels through it so eavesdroppers cannot access it. The process operates in the following simple manner:
- Your device begins a connection to the VPN server when you turn on the VPN service.
- The establishment of the tunnel occurs when VPN software creates a secure encrypted link with the server.
- Your device encrypts data through scrambling before it leaves so that any interceptors would remain incapable of deciphering it.
- Your encrypted data moves through the VPN server after passing through a tunnel.
- The VPN server handles data decryption before it forwards the information to its proper internet destination.
- The response travels back to your device through the tunnel after the VPN server encrypts it before your VPN software decrypts the data.
The multiple steps enable you to protect your privacy and data security when using networks that cannot guarantee security.
What Is Encryption?
The conversion of information into coded data through encryption operates as a protection method against unauthorized access. Writing with an encrypted code functions like composing messages that can be decoded by you and your trusted individual alone. The encryption process converts data into a jumbled format which appears as random characters. Anyone without the appropriate key or password cannot transform the scrambled data into its original format.
How Encryption Protects Your Data
The protection of your data through a VPN depends heavily on encryption functions. The following points explain why this protection method matters so much:
- The encryption method creates an unreadable data state which protects your information from interception even when someone gains access to it.
- A VPN utilizes encryption to shield passwords along with bank details and personal messages from cybercriminals who try to steal them.
- Through encryption, you achieve data integrity because unauthorized modifications are prevented, thus maintaining accurate data consistency.
- The encryption process enables VPNs to conceal your online identity so third parties find it more difficult to track your activities across the internet.
Encryption converts readable data into special operational codes which function for only authorized devices to read. The encryption system functions similarly to a safe which requires your exclusive key for access.
What Is Tunnelling?
VPNs transmit your protected information to the internet using a process known as tunnelling. A physical pathway exists which surrounds users and defends them from outside elements when they travel. A VPN tunnel operates as a virtual protected route which secures your data from observation throughout its route from your device to the VPN server and onward to the internet.
How Tunnelling Works in a VPN
A secure tunnel between your device and the VPN server is formed when you connect to the VPN service. Specialized protocols create the tunnel by determining how data will be both encapsulated and transmitted. The VPN working mechanism is divided into two fundamental actions:
- The data receives protection through added information layers. The additional layer contains information about the destination path while providing security to data as it travels.
- The encrypted data which passes through the secure tunnel reaches its destination at the VPN server. The safe transmission of data occurs because the protective layer covers it, thus making any intercepted data impossible to access.
The VPN server receives data which is decrypted by unpacking it before passing the information to its destination point. The secure data transmission process operates in the reverse direction for the return of data to preserve complete confidentiality of communication.
Common VPN Protocols
The creation and management of secure tunnels between devices and VPN servers depend on the different protocols which VPNs employ. The most frequently used VPN protocols consist of:
- OpenVPN functions as an open-source protocol which delivers strong security while maintaining high flexibility. OpenVPN has become popular because it successfully circumvents common firewalls while delivering secure defence capabilities.
- The Internet Protocol Security Suite, or IPSec, protects Internet communication through the authentication and encryption of all IP packets.
- L2TP with IPSec provides secure, secure, and reliable access from your system to the VPN server. It creates a data tunnel in advance before encrypting it using IPSec.
- WireGuard stands out as a contemporary protocol which experts appreciate because of its basic design and exceptional speed capabilities. The secure encryption and protection functions of this protocol are protected by its contemporary design structure.
A particular protocol gets selected based on user requirements because each one brings different benefits to the table. Users choose OpenVPN because of its adaptability and strong security elements, yet they prefer WireGuard because it delivers fast performance.
Benefits of Using a VPN
VPNs supply various advantages which justify their status as fundamental tools used by numerous internet users. The main benefits of VPNs consist of:
- Your IP address stays hidden, and data encryption protects your activities from tracking attempts by websites, hackers, and government agencies.
- The encryption capabilities of a VPN create a protective shield which defends your data from hacker attacks during your usage of public Wi-Fi networks as well as other malicious software.
- A VPN provides you with access to content that censorship and geographical restrictions keep users from accessing. The service permits you to watch websites and streaming websites that restrict content in your region.
- Businesses utilize VPNs to create secure remote connections for their private networks, hence enabling their workers to work from home securely.
- Internet service providers can reduce speeds on specific types of traffic but bandwidth throttling is VPN-proof. Bandwidth throttling can be avoided with a VPN since it conceals your internet activities.
Conclusion
In the current digital environment, VPNs provide essential protection to users. The secure encrypted tunnel created by VPN services gives you both privacy defence and anonymous characteristics while using the internet. VPN operates through encryption and tunnelling technologies which together defend your information from unauthorized viewers and hackers.
Your knowledge of VPN operation enables you to select a service that fits your security requirements. A VPN offers protection for your data and mental serenity through online usage, regardless of your internet consumer level or data sensitivity.